
- A Gentle Introduction
- IP Addresses for Internet Privacy and Security
- How to Hide Your IP Address: Proxy vs VPN vs TOR.
- How Proxies Work
- How VPNs Work
- How TOR Works
- HTTP vs HTTPS
- Tips for Safely Using Email
- What to Do if You Accidentally Clicked on a Suspicious Link in an Email
- Bonus: The Two IP Versions: IPv4 vs IPv6
A Gentle Introduction
You've probably heard of IP addresses before but may be unclear on what practical knowledge you should have about them. You don't need to know the nitty-gritty about how physical addresses work, why should you for virtual addresses!
When you address a package or write a letter, the postal service uses the physical address to know where it should go.
When you go to a website or send an email, the internet service provider uses the virtual address to know where it should go.
An IP (internet protocol) address is a number assigned to every device that is connected to the internet. Internet service providers (ISPs) maintain a large pool of IP addresses. In exchange for your monthly payment, you are allocated one each time you go online. For example, your current IP is 18.222.142.215 which appears to be provided by an unknown provider.
ISP availability usually depends on where you are. Popular ISPs include Comcast, Time Warner Cable, Cox Communications and AT&T. Generally the main difference between the providers is speed (Mb/s), price, and volume which is measured in bandwidth (GB/mo). Here are some more examples of IP addresses:
- 192.168.56.101 - This is a private IP meaning it is only used for local area networks (LANs) in offices and homes.
- 127.0.0.1- The "localhost" or "loopback" IP, this refers to your own computer. Traffic sent from your computer to this address is immediately received right back to your computer. Perhaps you have seen the T-shirt with the phrase "There's no place like 127.0.0.1." 127.0.0.1 here refers to "home".
- 51.89.155.27 - A random public IPv4 (version 4) address. We briefly discuss v4 vs. v6 at the end.
- 2485:b5e0:90ba:2472:b6f6:3d1d:7e01:a0e6 - A random public IPv6 (version 6) address. These are longer, newer, bigger, better.
- ::1 - IPv6 version of localhost. Note the "::" represents consecutive blocks of 0s so ::1 is actually short for 0000:0000:0000:0000:0000:0000:0000:0001
- 172.16.0.0/16 - This is a block of IP addresses. The "/16" is called CIDR (classless inter-domain routing) notation and means "the first 16 bits of this IP address are fixed, the rest are wild." In other words this refers to all IP addresses of the form 172.16.[0-255].[0-255] (e.x. 172.16.31.216, 172.16.211.255, ...). Most users won't come across these in the wild. CIDR notation is also applicable for IPv6 addresses.
When you turn on your computer or phone and connect to the internet, your ISP assigns you a public IPv4 or IPv6 address. While you are online, this is your digital fingerprint. Often if you change networks, go to a coffee shop or are offline for a few hours and then sign-on again your IP will change because most people have a dynamic IP. Unless you check, you won't notice any difference. You can also buy a static IP from your ISP so it won't change even if you log off. These are useful when you want people to access your computer such as when hosting a website or game server. If your IP is static, you only have to tell your users what your IP is once.
IP Addresses for Internet Privacy and Security.
Ok, you know what an IP looks like, and that your ISP gives you one. What practical knowledge do you need? Perhaps the most important part: almost all of your internet activity is tracked, stored and identified by your IP address at the time of browsing. For example, when you access a company's website, your IP (and a lot of other information) shows up in their server logs. Some companies rotate their logs every few days, many keep them for years. Companies sometimes include a data retention policy in their privacy policy detailing how long they keep their logs.
There is some good news. A lot of the information stored is technical and not personally identifiable. Usually the most identifiable piece of information that you provide in a web request is your IP. This is why many webmasters impose IP-based rate limits or block IP ranges if they are flagged as malicious. IPs make decent short-term IDs for blocking but not so good long-term IDs because it might change hands from a malicious user. Tracing an IP back to the ASN (autonomous system number), ISP, or country is often the first step to combat DDOS (distributed denial of service) attacks.
Similar to how if someone has your address they can run a reverse address lookup to find information about who lives there, if someone has your IP address they can run a reverse IP lookup to find information about who is using or has used the IP.
However unlike an address, IPs change frequently and the data may not always be up-to-date. In fact, IPs change so frequently that some industries don't even consider it personally identifiable information (PII). Unless the ISP is issued a subpoena for the exact records, it's difficult to verify that the person you found owned the IP address at the time you received it; maybe it's the previous owner. In any-case if someone has access to the server logs, information they can trace back to you may include:
- Your browser history on that website.
- The amount of time you spent on each page.
- The files you downloaded or uploaded
- The videos you watched.
- What you clicked.
- High-level information about your computer including the browser, operating system and device type.
How to Hide Your IP Address: Proxy vs VPN vs TOR.
There are several options to conceal your real IP and conceal your internet usage from hackers who might be watching for unencrypted traffic. Here is a simplified version of how traffic is normally routed and how your IP address changes:
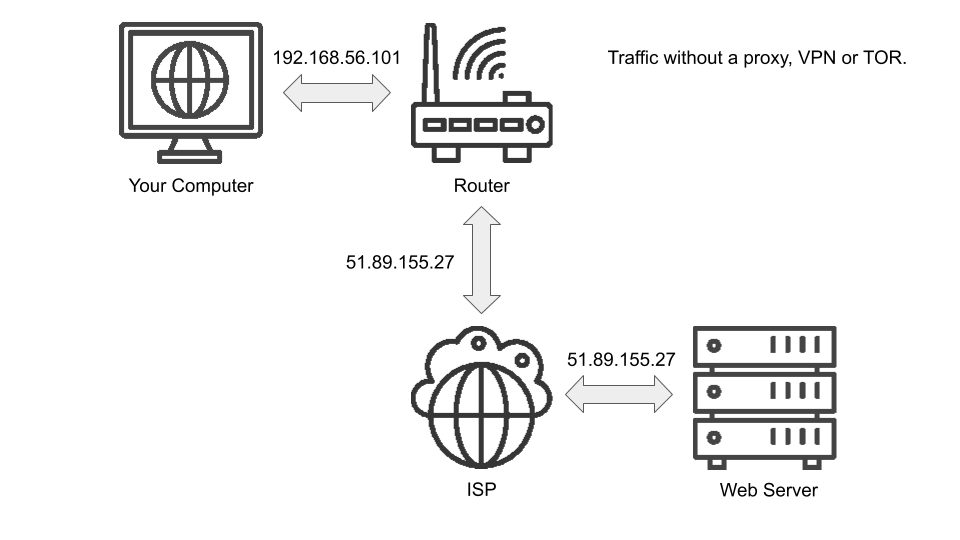
You could use a proxy, a VPN (virtual private network) or TOR (the onion router). Which you use is up to you. Here is a brief overview of how they work.
How Proxies Work.
Proxies are the simplest. They serve as a middle ground between you and the website (or internet resource) you are requesting. Instead of requesting a website directly, you configure your browser to send the request to the proxy which swaps out the IP address in the request for its own and then forwards the request. This means it looks to the website like the request came from the proxy, not you. The website then responds to the proxy with the results of the request and the proxy returns it back to you. Here's an overview of how your IP travels:
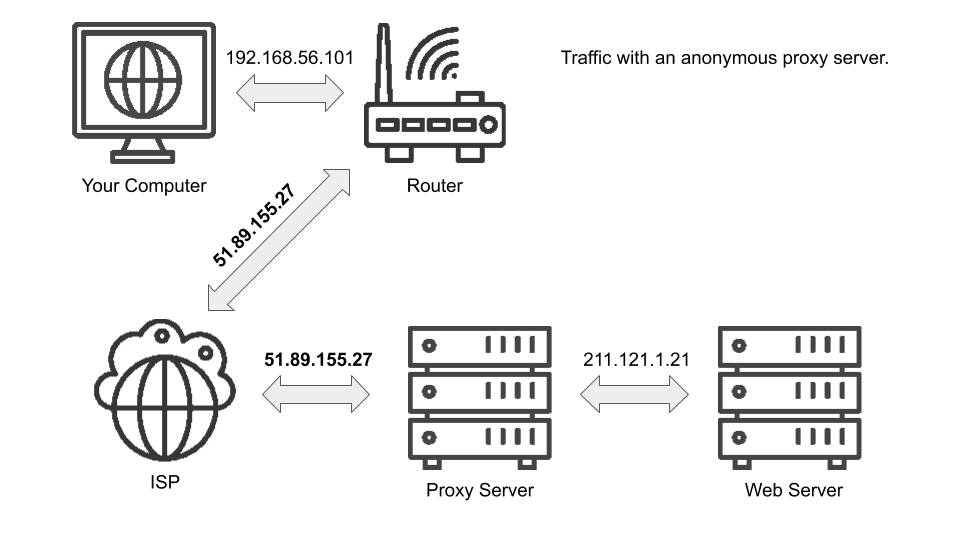
There are several free proxy options but be wary; not all proxies, especially the free ones, are completely anonymous. A non-anonymous proxy still includes your IP in the request to the website. These are used primarily for caching purposes, not privacy purposes. If you use a proxy, you need one with a high or elite anonymity rating. You can test if the proxy is working by setting up your browser to use the proxy and then going to http://httpbin.org/anything. All you should see is the proxy IP on the "origin" field. If you see your real IP address anywhere, you are not browsing anonymously. Also keep in mind some free proxies have non-favorable logging policies; you may be still tracked but at the proxy level not the website level. Be sure to look for any disclaimers, privacy policies or terms of service that the proxy website provides.
Bottom Line: Proxies are usually free but sort of "quick-and-dirty." Best to only use these if you know what you are doing.
How VPNs Work.
VPNs are sort of like proxies but they differ in three major respects. First, they are usually set up with the express intention of protecting your privacy. It is easier to misuse a proxy thinking you are protected than it is to misuse a VPN thinking you are protected. Second, VPNs encrypt the traffic you send so your internet service provider or anyone listening in will only see that you are connecting to a VPN; they will not see what you are doing. Finally, VPNs protect all of the network traffic coming from your computer. Proxies are often set on the application level meaning if you configure Google Chrome to send traffic through a proxy but later use Firefox, Firefox will still be routing traffic directly to the site with no privacy protection. Like proxies however, using a VPN is a good way to change the country your request originates from. This can be useful if you are trying to access a website from a country that has blocked you. Here's a simplified overview of how VPNs protect your IP and browsing requests:
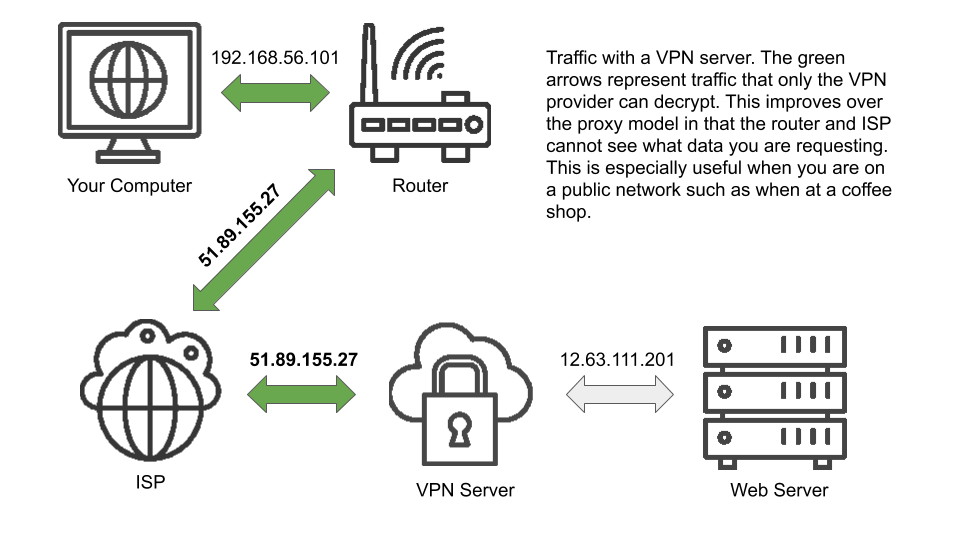
Bottom Line: VPNs are usually safer, more fool-proof, and the recommended way to protect your internet traffic. Look for VPNs with a no-log policy. Respected VPN providers include NordVPN, ExpressVPN and TunnelBear. Don't use a free one, it's free for probably not a good reason.
How TOR Works.
TOR is a method of anonymous browsing that works by wrapping your request up into an encrypted "onion" and then sending it through a network of several TOR nodes. Along the way, each node peels back one layer on the encrypted onion until it gets to "core" which is your unencrypted data. The unencrypted core is then sent off to the website you originally requested. Crucially, along the way each TOR node only sees the IP address of the previous node and the next node. This means that only the entry node knows your IP but it has no idea where your data is off to. It simply knows which node in the TOR network it should send the peeled back (but still encrypted) message to. Once the message reaches the last node, called the "exit-node," the request is sent to the website but it appears as though it's coming from the exit-node. There are issues using TOR. ISPs or websites may block TOR traffic. To get around ISP blocks, you can first connect to a VPN and then use a TOR browser because a VPN will hide the traffic from the ISP. There are several dangers using TOR, however and it is generally slow. Using a VPN without TOR is sufficient for most users. Here's a simplified overview of how TOR works:
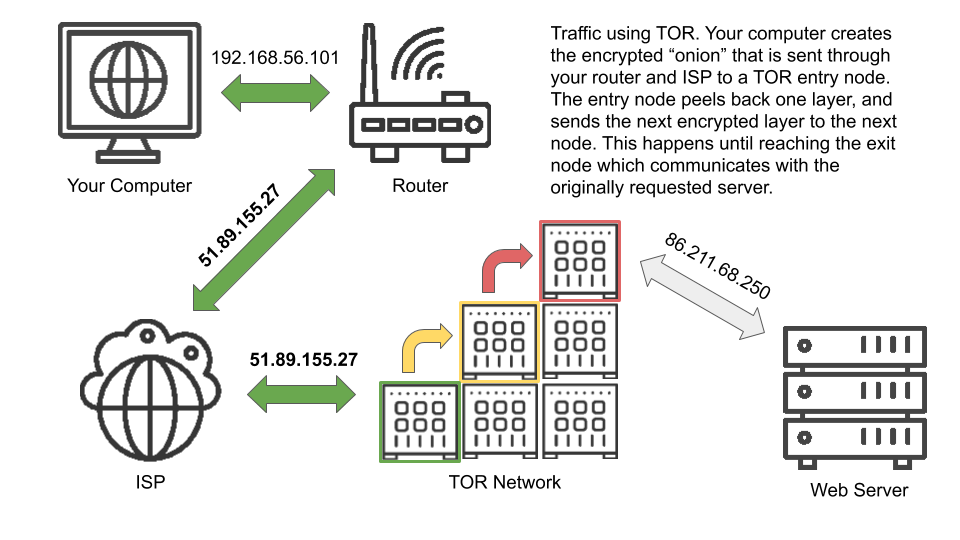
Bottom Line: TOR is more dangerous, slower and less reliable than a VPN. While it has many practical uses, it is not recommended for most users.
HTTP vs HTTPS.
So you've signed up for a VPN. Your IP is hidden and your traffic is encrypted right? Wrong! A VPN may encrypt the traffic between you and the provider but it doesn't necessarily encrypt the traffic between the provider and the website. This is where HTTP vs HTTPS comes in. Even for users not using a VPN, the distinction is important. HTTPS (HTTP secure) is simply encrypted HTTP. If you are accessing a website over plain old HTTP and send a username or password, that information is being transferred across the internet in plaintext. If you are on a VPN, it will only be plaintext in-transit from the VPN provider to the website.
Whenever giving important credentials it is important to make sure the url starts with "https://" and the browser recognizes the website as secure with a lock:

This means any traffic you send to the website will be properly encrypted. Sometimes you may find the url starts with "https://" but the browser warns you that it is "not secure:"
This means that your traffic may be encrypted but your browser does not recognize the website as being the "real" version. This is a major red flag, you should not enter any information especially if it's on a website that you are familiar with — something fishy is afoot. Also bear in mind that even with HTTPS, your IP address and the domain (or IP) of the website you are requesting is not encrypted. Remember, if you want to hide your IP you should use a VPN, proxy or TOR.
Tips for Safely Using Email.
Emails are a very common source of scams. There are a few rules of thumb you should be aware of when browsing email.
- Any unsolicited email asking for money, passwords or other sensitive information should be regarded as highly suspicious. Do not click on any links in the email and the scammer will not pass go.
- Many email clients let you view the raw original email text by clicking "view original." There is a ton of information here, you want to find "Received: from ... (... [<IPAddress>])" and then can run a reverse IP lookup. To find this in Gmail:
First, In Gmail, open the email and click the three dots on the right hand side:
Then, click "Show Original" from the dropdown menu:
Finally, find "Received: from ... (... [<IP Address>])" - Any email suggesting you won something, are the 10 millionth viewer, or has a lot of confetti is probably a scam. Don't click on any links...
- Sometimes scammers will register domains that look like the reputable website like "bankofam3rica.com" and will be able to send you a legitimate looking email from "alerts@bankofam3rica.com". These fake emails can look identical to the real emails. Double and triple check that the domain on the "from" address is something you recognize and is exactly the same as what you expect. For example, if you have an account at Bank of America and receive an email with a from address "alerts@bankofam3rica.com," do not click on any links!
Rule of Thumb: Do not click links in emails!
What to Do if You Accidentally Clicked on a Suspicious Link in an Email.
First of all, make sure your browser identifies the website as being trusted and secure (see HTTP vs HTTPS section). It is possible to make fake websites that look identical to the original but not possible to trick the browser into thinking you are on the original. If you have been tricked and ended up on a scam website, don't worry the worst case is they can now associate your IP with your email address and can verify there is an active recipient at your email address. This is usually not a major security concern.
If you click on a link and accidently typed information into a form such as a password or credit card information before realizing it was a fake website, this is a major security breach. You should consider your password to be compromised and change it on all websites. If you put in financial information you should contact your bank immediately.
Bonus: The Two IP Versions: IPv4 vs IPv6.
IPv4 (IP version 4) was the first generation of IP addresses with IPv6 (IP version 6) coming shortly after realizing the 4,294,967,296 available IPv4 addresses (many pre-reserved for special use) would quickly run out. IPv4 addresses are 32 bits long (4 bytes) and are represented as four one-byte numbers such as 192.168.56.101. Many IPv4 addresses such as 127.0.0.1 (referring to your own computer also called localhost or loopback) have special use cases and are not given out by ISPs. You may also sometimes see IPv4 addresses followed by a forward-slash and a number such as 192.168.0.0/16. This is called CIDR (classless inter-domain routing) notation and is used to represent a block of IP addresses. The number following the forward-slash represents the number of bits that are "fixed" in the IP, the rest are wild. For example, 192.168.0.0/16 can be read as "any IP address starting with 192.168" because the first two numbers compose the 16 fixed bits. For a trickier example, 209.51.241.0/20 has 20 bits fixed. Another way to write 209.51.241.0 in binary (base 2) is 11010001.00110011.11110001.00000000. The first 20 bits (in bold) are fixed which means any IP address that has the same first 20 bits is in that CIDR block.
The internet has only recently begun serious movement on adopting IPv6 addresses. While IPv4 offers approximately 4.3 billion addresses with 32 bits, IPv6 uses 128 bits allowing for 2^128 or 340,282,366,920,938,463,463,374,607,431,768,211,456 addresses. That's 340 undecillion or... a lot. The 128 IPv6 bits are represented using hexadecimal (base 16) where every 2 digits corresponds to 8 bits so the total address is 16 groups of 2 or 8 groups of 4. For example, 2485:b5e0:90ba:2472:b6f6:3d1d:7e01:a0e6 is an internet-facing IPv6 address and ::1 is the localhost address. Note two colons in an IPv6 address are used to abbreviate 0s so ::1 in long-form is 0000:0000:0000:0000:0000:0000:0000:0001. IPv6 also allows leading 0s to be omitted so ::1 can also be written as 0:0:0:0:0:0:0:1.
If you have any questions or would like to suggest a topic we should cover in our next post, please contact us at info@thatsthem.com. Feel free to share this article if you found it helpful!
Back to Posts
